Standard Access List (ACL) for the Cisco CCNA - Part 2
ฝัง
- เผยแพร่เมื่อ 27 ก.พ. 2012
- A beginner's tutorial on writing a standard access list (standard ACL) for the Cisco CCNA and CCNA Security. The demonstration uses the Cisco Packet Tracer software.
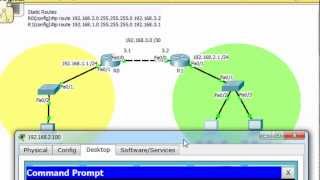
In part 2, I continue to discuss access list fundamentals. How the router reads an access list line by line and permits or denies traffic based on a match. I show how to remove an access lists, append a line to an access list and how access lists statements need to be written from specific to general. Click here for part 1: • Standard Access List (...
Please send feedback and subscribe! For more information on this topic, visit me at danscourses.com








This man is a CCNA RS teaching genius. You can do what few others can. You have a true gift. I never thought ACL would get me excited, but you make it so effortless.
He's one of the best at explaining how things work with Cisco. I would recommend his teachings to anyone who wants a CCNA certification. I can't say enough or give him more accolades because of all the comments below.Please keep up the great work.
All CCNA courses should be teached in this way, THANKS !!!
Great tutorials! Massive help for my ICND2 exam. I found though that instead of creating a new ACL, it was easier to go into ip access-list standard and do a no permit any. and then added it back in again to send it to the bottom :). Hope this helps anyone wondering if that sort of thing is possible. These videos are unbelieveably good though for studying. You're a life saver :)
Thanks Dan, I spent a day trying to figure out how access lists work, after this video everything seems to me much clearer. I can see clearly now the rain is gone :)
I went from being completely clueless to actually understanding what this does. And I’m not even done with the video yet.
You are amazing at teaching. Wish you were my teacher.
I don't know if this is because this video was made in 2012 but now you can go in the access list and squeeze the rule in the middle like this:
R0(config)ip access-list standard 1
R0(config-std-nacl)15 deny host 192.168.2.191
The 15 in front of the command is in case the first and the last rules are 10 and 20 respectively
Dan, your explanations are so clear. From the basics to advanced features, they are very complete and very logically built up. Thank you very much. They inspire and give confidence. Kind regards, TvdTooren
This video is great and makes ACLs easier to understand.
Hi Dan,Please do not give up with your Videos.Much appreciated ! :-)
for those having experience in iptables, this should be piece of cake. it's basically the same as iptables, with the same design principles applying, with the difference that in iptables you can insert a rule in a specific point, and the "access-list X deny any" is the same as the default policy of a chain in iptables.
easy!
You are amazing. How you make it so clean is a gift
thanks for explaining in such detail....this helped a lot..thanks..
You great n easy to understand thank you ! We
Need more updated version of CCNA
Well explained, and illustrated, thanks a lot...
You are the best lecture,thanks
Thanks from my whole heart sir
thank u very much for dis video good work...
Great teacher. Thanks a lot.
amazing exactly to the point. thank you very much
Thanks Man! You da best Bruh!
that was helpful!! thanks a ton!
wonderful titural !
thank you man
great job thanks
Thank you for videos.
thanks sir god bless you
Thanks Dan, this helps me a lot ,,,
I have understand a lot from you than my bad tutor
cheers
Hi,
What if you do this:
access-list 99 permit 192.168.2.0 0.0.0.255
access-list 11 deny any
interface fa0/1
ip access-group 11 out
exit
Does this mean that, access-list 99 will be denied, or if we didnt implement the acl in interface, the packets will be allowed?
Thank you for the tutorial.
interesting fact about the default "deny any": if you create an empty access list by typing "
access-list 98 remark deny test" and you apply it it to an interface, the traffic won't be blocked.
thanks
awesome
Thank you for the video sir!
Is it possible for me to permit one host and deny any other?
yes! permit the one host first then deny the whole network second
hey dan,
I wanted the answers of the activity of standard ACL,
could you just provide that.
becoz i am trying to figure out what went wrong,if you could pls,write down the commands
I watch your videos and like your teaching method, I ended up here and amazingly landed at exactly point of the video I needed delete an ACL. But I I've been trying for hours to delete a standard named ACL it just won't go away. Tried "no access-list 1" even though it doesn't have a number. I tried "no access-list standard NameofList" (not literally NameofList but the actual name I gave my list). I can't edit it and I can't delete it I'm stuck.
Sounds like a glitch in Packet Tracer. Save your file, close it and restart it.
Can we ping from the denied host ?
Which playlist is this vidoe included in?
can we ping from denied host and vice versa
To block 192.168.2.100 you can also just remove the command: ip access-list 1 permit any
R1#conf
Configuring from terminal, memory, or network [terminal]?
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#
simply press "Enter" one more time
it didnt happend in gns3 ..
when i added the access list later the run config arranged it like -=
access-list 1 deny 10.1.1.10
access-list 1 deny 11.1.1.10
access-list 1 permit any
n the filter is working .. why ?
i hope u have an option to edit acl instead of rewriting the acl.
by the time u said no no acl all users get the full access for that bit of time.
Misbah Mohammed Good point. There are options to edit ACLs inline. Zone Based Firewalls are the way to go nowadays.
Hello Sir Dan,
I have tried doing this and I have a question for you or for someone that knows the answer. I have configured the routers exactly as the video suggest.
In the video, you've put the, "access-group 1 out" in Fa 0/1 of R0.
Now, I tried to ping 192.168.1.100 (Destination Host) using the PC with an IP of 192.168.2.101(Denied Host). The result was unreachable which is the correct result.
Now, I tried the other way around and used 192.168.1.100 (Destination Host) to ping the 192.168.2.101 (Denied Host). Well, it's unreachable.
Since the, "access-group 1 out" is configured in R0 int Fa 0/1, It should just only filter traffic coming from the outside, right? So my Ping request should be permitted, but I'm getting the unreachable response.
I would really appreciate a help on this one.
Thanks.
Roids For COC Hi roids. The reason your ping isn't succeeding is because it's a 2-way communication. So it's going out of the router and reaching the denied host, but when it tries to come back from the denied host, it's getting blocked at the router. Hope that helps!
Ohh.... I see ... Thanks Matthew.
***** so if that is the case how can I configure a router to do something like this, I want the 1 network to be able to talk to the two network but not have the 2 network talk to the 1 network, is this possible?
Douglas Howe I have no idea to be honest.
+Douglas Howe if talk refers to ping, you can use an extended access-list to block inbound icmp packets to lets say R1, so when R2 and R3 ping R1 no reply, but R1 pinging R2 and R3 outbound its going to have a reply.......Lab it up and tell me the result if you don't mind
GReat
And if we only tap the command of permit a host, the others will be deny automatically !? so why write dny avery time
maybe you should specify wildcard bits after ip.
#access-list 1 deny 10.1.1.10 0.0.0.0
#access-list 1 deny 11.1.1.10 0.0.0.0
Hey Dan why when you type no access-list 1. it remove it but the ip access-group 1 stays there?
because he removed the access-list from the router, not access-group, if you make a new access list with the same number, it will be already applied on the interface
If you were to just create access-list 99, and then add "allow 192.168.2.100", cant then apply that to the interface - that should be all you need.
Because of the implicit deny any. This would essentially ONLY allow the 1 host you want, and deny everything else.
KISS.
this would deny everyone except the 2.100, you gotta ask yourself whether you want to only allow one computer to connect to your network or you want everyone to connect to your network except one computer
let me save some pain for the viewers by letting them know that you can type "do sh run" to show the running-config instead of going all the way back to R#. Maybe the poster was working with an older IOS that doesn't support this command. Im new myself, so I'm not pointing any fingers
pardon it is not .2.100 but .2.101
really dont understand why im going to university for 💀
Extremely repetitive....too many RIGHT questions...