Double ratchet algorithm: The ping-pong game encrypting Signal and WhatsApp
ฝัง
- เผยแพร่เมื่อ 5 ส.ค. 2022
- How do text messaging services like Signal and WhatsApp keep your text messages secure? The Double Ratchet algorithm.
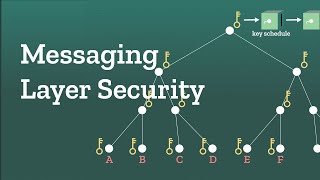
Let’s say Alice wants to send Bob an end-to-end encrypted message. She uses a key to lock up the message and Bob uses the same key to unlock the message. But what if they want to send a bunch of messages back and forth? Using the same key the whole time is not very secure. It would be better to have a unique key for each message. The Double Ratchet algorithm cranks out a new key each time you send a message by combining a key derivation function and a Diffie-Hellman calculation.
Resources:
Diffie-Hellman (with numbers): • The Mathematics of Dif...
Diffie-Hellman (with colors): • Secret Key Exchange (D...
Signal Specifications: signal.org/docs/specification...
Created by Kelsey Houston-Edwards
Sponsored by Wire wire.com






![เปิดบ้าน เปิด Supercar อั๋นโอกิ เคยเอา rolls Royce เเลกพระ องค์ละ 100 ล้าน l [Nickynachat]](http://i.ytimg.com/vi/FeGwJwXauZ0/mqdefault.jpg)

How are these videos under 1k views? This is the best explanation I've seen in TH-cam about this topic
Agreed
because she left Infinity :(
@@EmperorZelos that was years ago, and still it doesn't explain how come these videos have not blown up
So glad you are back on TH-cam! Your infinite series videos are in the very top tier of math education. There are very few people that can teach math as well as you can.
This is probably the best explanation I've seen for any topic, ever.
Happy you are back!!!!!😍🥰😍😍😍😍
this is hands down the best explanation I've come across. thank you sm
Wow such a surprise. Great to learn from you after long time.
this explanation was incredibly clear. Thank you
BEST EXPLAINATION EVER, I SWEAR!
Great video! You're so pleasant to listen to, and concise
This was so helpful, thanks for taking the time to make this very understandable.
Thank you so much for this. I was having a hard time understanding how the double ratchet was tied to diffie hellman. The symmetric encryption and decryption with the shared key makes a lot of sense.
May I ask, if you don't mind, how does the ephemeral key and multiple prekeys fit into this double ratchet? I suspect the ephemeral key is similar to a session key which is re-generated every time the user comes back online. But how about the prekeys? If the key derivation function is not updated, how are the prekeys used?
Best and Simple explanation
The best 👍
This type of content restored my faith in the internet and TH-cam. Thank you very much could you recommend courses/ books for those who are interested in advanced cryptography subjects
8:43 I dont understand something. Alice lost her first priv/pub key pair after response. how can she decrypt previous messages?
How would the system re-sort messages received out of order? I dont get it. If Alice received Bobs message out of order, and say after Alice sent her own messages, then all the machinery would have changed and you couldnt decode the out of synch messages.
The solution for this would be to retain memory of the prior keys.... but I imagine that would compromise security both backward and forward
thx
What if bob user want's Old messages.
And bob switch to another phone than how he can decrypt unread messages
He can‘t, like with Signal App. He also can‘t on whatsapp, but whatsapp requests the sender to resend messages wich were marked „unreceived“ (only one ✅) with the new keys.
How do you perform DH if your peer is offline?
Every participant puts some public keys in advance to the Server (Signal, Whatsapp).
The sender retrieves one of those, mixes it with his private key and sends the encrypted message with his publics key to the receiver. The receiver starts to mix his private key with the public key from the sender and gets the shared secret to decrypt.
Well, if you gain access to Alice or Bob's private key, you see everything. Why is worry more focused on defending from the attacker getting access to one of the intermediate secret keys that encrypt the message rather than the base private key that Bob and Alice have that never changes?
In other words why is it considered more likely that the key that encrypts the message will be compromised rather than the base key that each Bob and Alice have that never changes?
because the secret key should never leave the device
0:10
Let me get this straight... we are just using Diffie Hellman on each message? This doesnt seem particularly special in and of itself.
HELP
Who you no make more vids?
Wow, this channel is on par with @Computerphile. Subbed! 🎉