
- 5
- 92 715
Chalk Talk
เข้าร่วมเมื่อ 9 มิ.ย. 2022
Math, computer science, physics, etc.
Made by Kelsey Houston-Edwards
www.kelseyhoustonedwards.com
Made by Kelsey Houston-Edwards
www.kelseyhoustonedwards.com
Learning with errors: Encrypting with unsolvable equations
Yes, you can use the language of linear algebra (matrices, dot products) to discuss lattices and learning with errors. Check out the resources below for more information.
Created by Kelsey Houston-Edwards (www.kelseyhoustonedwards.com)
Sponsored by Wire (www.wire.com)
________
Post-Quantum Cryptography: th-cam.com/video/_C5dkUiiQnw/w-d-xo.html
Lattice-Based Cryptography: th-cam.com/video/QDdOoYdb748/w-d-xo.html
________
Timestamps
0:00 - Introduction
0:35 - Learning without errors
1:58 - Introducing errors
3:36 - Modular arithmetic
3:59 - Encrypting 0 or 1
7:14 - Relationship to lattices
________
Modular arithmetic (wiki): en.wikipedia.org/wiki/Modular_arithmetic
Modular arithmetic (Khan Academy): www.khanacademy.org/computing/computer-science/cryptography/modarithmetic/a/what-is-modular-arithmetic
Modular arithmetic (video, blackpenredpen): th-cam.com/video/6dZLq77gSGU/w-d-xo.html
LWE (expository notes): cims.nyu.edu/~regev/papers/lwesurvey.pdf
LWE (lecture): th-cam.com/video/K_fNK04yG4o/w-d-xo.html
Encryption from LWE (lecture notes): courses.grainger.illinois.edu/cs598dk/fa2019/Files/lecture10.pdf
Kyber (website): pq-crystals.org/kyber/index.shtml
Created by Kelsey Houston-Edwards (www.kelseyhoustonedwards.com)
Sponsored by Wire (www.wire.com)
________
Post-Quantum Cryptography: th-cam.com/video/_C5dkUiiQnw/w-d-xo.html
Lattice-Based Cryptography: th-cam.com/video/QDdOoYdb748/w-d-xo.html
________
Timestamps
0:00 - Introduction
0:35 - Learning without errors
1:58 - Introducing errors
3:36 - Modular arithmetic
3:59 - Encrypting 0 or 1
7:14 - Relationship to lattices
________
Modular arithmetic (wiki): en.wikipedia.org/wiki/Modular_arithmetic
Modular arithmetic (Khan Academy): www.khanacademy.org/computing/computer-science/cryptography/modarithmetic/a/what-is-modular-arithmetic
Modular arithmetic (video, blackpenredpen): th-cam.com/video/6dZLq77gSGU/w-d-xo.html
LWE (expository notes): cims.nyu.edu/~regev/papers/lwesurvey.pdf
LWE (lecture): th-cam.com/video/K_fNK04yG4o/w-d-xo.html
Encryption from LWE (lecture notes): courses.grainger.illinois.edu/cs598dk/fa2019/Files/lecture10.pdf
Kyber (website): pq-crystals.org/kyber/index.shtml
มุมมอง: 22 855
วีดีโอ
Lattice-based cryptography: The tricky math of dots
มุมมอง 37Kปีที่แล้ว
Lattices are seemingly simple patterns of dots. But they are the basis for some seriously hard math problems. Created by Kelsey Houston-Edwards (www.kelseyhoustonedwards.com) Sponsored by Wire (www.wire.com) Post-Quantum Cryptography: th-cam.com/video/_C5dkUiiQnw/w-d-xo.html Learning with Errors: Coming January 5, 2023 Timestamps 0:00 - Post-quantum cryptography introduction 0:58 - Basis vector...
Post-quantum cryptography: Security after Shor’s algorithm
มุมมอง 15Kปีที่แล้ว
What’s the current status of the NIST Post-Quantum Cryptography Standardization? Find out here: csrc.nist.gov/Projects/Post-Quantum-Cryptography Created by Kelsey Houston-Edwards (www.kelseyhoustonedwards.com) Sponsored by Wire (www.wire.com) Lattice-Based Cryptography: th-cam.com/video/QDdOoYdb748/w-d-xo.html Learning with Errors: Coming Jan 5, 2023 Timestamps 0:00 - National Institute of Stan...
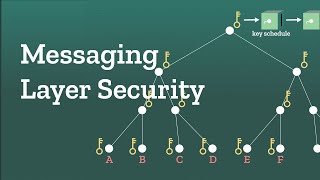
Messaging layer security: Encrypting a group chat
มุมมอง 8Kปีที่แล้ว
How do you keep the messages in a group chat secure? Messaging layer security (MLS). The Double Ratchet algorithm provides end-to-end encryption for text messages between two people. But securing a group chat is much harder. MLS is the first standardized multi-party “key exchange” - a protocol for communication among groups of people or devices. Resources: Video on the Double Ratchet algorithm:...
Double ratchet algorithm: The ping-pong game encrypting Signal and WhatsApp
มุมมอง 10Kปีที่แล้ว
How do text messaging services like Signal and WhatsApp keep your text messages secure? The Double Ratchet algorithm. Let’s say Alice wants to send Bob an end-to-end encrypted message. She uses a key to lock up the message and Bob uses the same key to unlock the message. But what if they want to send a bunch of messages back and forth? Using the same key the whole time is not very secure. It wo...




the best explanation of lattice in youtube 🔥
nice work! thanks : )
What an amazing explanation!!! I believe you should teach Mathematicians how to teach!
noooooooooooo why are you gone again?!? why did I not find the channel earlier? whhhhhy edit: oh, I am so sad
This video is so cool 😎 thx
Well-articulated! Thank you.
Well-articulated! Thank you.
Well-articulated! Thank you.
This only works with very short messages. It’s not generalizable to, say, a one page letter. It’s equivalent to sending a blurry image that the recipient can sharpen but so could a mitm. I’m not so sure this is as unsolvable as you think, and if it were, both Alice and Bob would need a way to share the actual errors securely in the future.
such a beautifully well done video. Thank you for taking an intimidating concept and making it accessible.
this was amazing!
very pleasant to watch.
What about AES 256?
5:15 but couldnt malkob(bobs bully) just calculate that 30x+67y+53z+24w=19(mod 89) is 0 and then check if it is equal to 0
Very clear explanation! Thank you!
Thank you so much. It's so simple and understandable
It is unclear how F gets its private key at 6'16''. It is also unclear why the rachet can go up the tree as well as down the tree.
I love you ❤
How are things supposed to be bruteforce proof if the decryption is supposed to offline
Always a joy listening to Dr. Houston-Edwards explain something complicated in a way that is approachable.
How do you create this kind of representation and animations of point lattices? I am writting a university project about post quantum cryptography, and I would like to introduce pictures and visualizations about lattices. Thanks :)
5:02
0:41
3:06
0:10
this short video series was very informative on learning the core of PQC algorithms. Especially since now apple after signal implemented a PQC algorithm.
c'est si clair et si bien expliqué. merci beaucoup !
First sponsorship I ever saw with less than 5k subscribers.
<3
Anyone know what happened to the channel? or where to find similar ed videos?
This was so helpful, thanks for taking the time to make this very understandable.
What happened to this channel? The videos were quite good and then they just stopped.
Love your videos and channel. Thank you❤
This video saved me a lot of time and confusion. Thank you so much for your great videos ♡♡♡
Great presentation! The basic concept of lattice-based cryptography looks simple which I think is good for analyzing it in terms of security.
This channel is wildly underrated!
When Bob adds 44 to encode a "1", how do we know that it results in a point that is far from all the lattice points? Is there an argument to show this?
Awesome video! Going with the intuition first without going into too much details. I wish to see more in the future.
The best 👍
00:00 - Introduction and the Challenge 00:54 - some Ideas how to solve it 00:54 - Parallelized Conversation 01:40 - Key Systems 02:17 - Messaging Layer Security (MLS) (Tree System) 03:37 - Key System 05:00 - Key Schedule 06:50 - Root Key change 09:53 - Remove Group Member 11:13 - Conclusion
wow..what a clear explanation of everything in such a short video. All my doubts are cleared now,. Thankyou
Regular people: just another thing to look at. Mathematician: why can't I make a mathematical model of this
Thanks! Would those noisy linear constraints be solved with linear regression?
Very good video, glad this is the first video that showed up when I searched for this topic
Could someone please share KYPER technique that perform the encryption and decryption?
Thank you so much! Video is intuitive enough to cover working principles of Post Quantum Cryptography. :)
Your videos are awesome! Very clear and informative.
😍 i'm in love. Who said maths arent Beautyful ?
So this has a major concern in my mind, while the math for this might be challenging when you step things up into more variables, there is also a deterministic quality to these problems when there is a large sample population of messages with the same secret key and mod. You would have to find a way to modify the secret key and mod and also communicate those changes over the network. This is ultimately the challenge, especially considering the passive listening that is happening over networks by state actors that have access to these large quantum computers. These problems will basically create a guaranteed back door for whoever controls the network and only really protect against people who are not the government.
amazing video, amazing series, and amazing effort. Thank you so much for the illustration, really helped so much.