Cross Origin Resource Sharing (CORS) Vulnerability | BugBountyTraining | Bug Bounty Service
ฝัง
- เผยแพร่เมื่อ 7 ก.ย. 2024
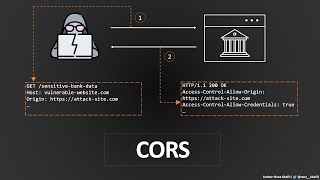
- This video shows how a misconfigured CORS can be leveraged to facilitate information disclosure.
Check out my courses:
1. The Ultimate Web Application Bug Bounty Hunting Course
www.udemy.com/...
2. Burp Suite Apprentice Web App Penetration Testing Course
www.udemy.com/...
3. Burp Suite Professional Web App Penetration Testing Course
www.udemy.com/...
4. Cyber Awareness Training
www.udemy.com/...








simple and crisp clear. THANKS!
Glad you liked it!
what if, the response has:
Access-Control-Allow-Origin: *
but, no "allow-credentials" popped on headers response.
Is like, vulnerable in a real case scenario?
That totally depends. In a Penetration Test it's a finding with low CVSS score. In Bug Bounty it's usually closed as informative however I had 2 companies pay me as a low. Normally they say in the Ts and Cs. CORS with impact. To pass cookies and make it impactful you need the allow credentials. Hope that makes sense?
Great explaination
Thanks
Thank you
How about CORS on POST request? Is that a vulnerability as well?
Yes absolutely. As a matter of fact you see CORS vulnerabilities often on POST requests
I find api subdomiNS BUT most of api endpoints are not accessible .
They probably need authentication. Most API endpoints will require some sort of authentication.
if the response says status302 not 200 is a serious vulnerability, can the attacker still take advantage of this ????
Not necessarily. A 302 is a temporary redirect. you should check how the redirect is initiated. If it's via "Location" usually you cant pull anything meaningful of. Sometimes however it will redirect via window.location and then you might be able to introduce XSS
If i find a cors bug but it's on POST request how do i exploit it???? please reply
For Bug Bounty you often don't need to exploit it and just report the reflected headers. Some will accept it and some won't. For impact it depends. Take a look at the CORS labs from the Web Security Academy. Typically you make an Ajax call from your own host to a sensitive (behind login) function
Cross origin Resorce bug
yes