DNS Enumeration And Zone Transfers
ฝัง
- เผยแพร่เมื่อ 21 ก.ค. 2024
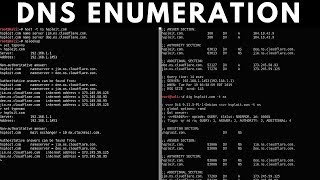
- In this video, I demonstrate how to perform DNS enumeration and zone transfers with host, dig, dnsenum, and fierce. DNS zone transfer, also sometimes known by the inducing DNS query type AXFR, is a type of DNS transaction. It is one of the many mechanisms available for administrators to replicate DNS databases across a set of DNS servers.
📈 SUPPORT US:
Patreon: / hackersploit
Merchandise: teespring.com/en-GB/stores/ha...
SOCIAL NETWORKS:
Reddit: / hackersploit
Twitter: / hackersploit
Instagram: / hackersploit
LinkedIn: / 18713892
WHERE YOU CAN FIND US ONLINE:
Blog: hsploit.com/
HackerSploit - Open Source Cybersecurity Training: hackersploit.org/
HackerSploit Academy: www.hackersploit.academy
HackerSploit Discord: / discord
LISTEN TO THE CYBERTALK PODCAST:
Spotify: open.spotify.com/show/6j0RhRi...
We hope you enjoyed the video and found value in the content. We value your feedback. If you have any questions or suggestions feel free to post them in the comments section or contact us directly via our social platforms.
Thanks for watching!
Благодарю за просмотр!
Kiitos katsomisesta
Danke fürs Zuschauen!
感谢您观看
Merci d'avoir regardé
Obrigado por assistir
دیکھنے کے لیے شکریہ
देखने के लिए धन्यवाद
Grazie per la visione
Gracias por ver
شكرا للمشاهدة
#DNS - วิทยาศาสตร์และเทคโนโลยี








We're following you from Mauritania 🇲🇷🔥
I like the way of your explanation and your English
My best youtuber thanks for your effort ... all love from egypt 🇪🇬
ترو
It's funny how after Egypt let go of Gaza (part of non-state, Palestine [a British name given to Jewish people for the right of return, and, P, doesn't exist in Arabic], after they rejected several very nice two-state solutions due to the publicly available charter that says to kill all Jewish people in the world, and all the speeches of Hama* to kill all Jewish people that has been recorded on video), for how bad it was with terrorism, made a wall to keep them out, and made the wall much larger after the October 7th terrorist attack.
Gaza is part of the non-state, Palestine even after Jewish people made most of the land habitable, made a multicultural land, and offered even 80% of the land.
RIP FH Astral Realms 💀 👻 to Ancient Egypt (even though that was blatantly a man-made religion like all the ones today). Iswrong took over, unfortunately so.
At least more apsotates are being made despite the command by Muhammad (peace not upon him) to *ill all apostates (Egypt just imprisoned one recently, I saw in the news). Now, public *ape is common to females, and so forth under tribalistic, Islamic influence.
At least not all Egyptians aren't religious. Near-death experience consensus shows most people leave cancerous religion and material atheism dogma (most atheists polled worldwide said they're spiritual).
Shalom.
It's funny how after Egypt let go of Gaza (part of non-state, Palestine [a British name given to Jewish people for the right of return, and, P, doesn't exist in Arabic], after they rejected several very nice two-state solutions due to the publicly available charter that says to kill all Jewish people in the world, and all the speeches of Hama* to kill all Jewish people that has been recorded on video), for how bad it was with terrorism, made a wall to keep them out, and made the wall much larger after the October 7th terrorist attack.
Gaza is part of the non-state, Palestine even after Jewish people made most of the land habitable, made a multicultural land, and offered even 80% of the land.
RIP FH Astral Realms 💀 👻 to Ancient Egypt (even though that was blatantly a man-made religion like all the ones today). Iswrong took over, unfortunately so.
At least more apsotates are being made despite the command by Muhammad (peace not upon him) to *ill all apostates (Egypt just imprisoned one recently, I saw in the news). Now, public *ape is common to females, and so forth under tribalistic, Islamic influence.
At least not all Egyptians aren't religious. Near-death experience consensus shows most people leave cancerous religion and material atheism dogma (most atheists polled worldwide said they're spiritual).
Shalom. @@seif9923
It's funny how after Egypt let go of Gaza (part of non-state, Palestine [a British name given to Jewish people for the right of return, and, P, doesn't exist in Arabic], after they rejected several very nice two-state solutions due to the publicly available charter that says to kill all Jewish people in the world, and all the speeches of Hama* to kill all Jewish people that has been recorded on video), for how bad it was with terrorism, made a wall to keep them out, and made the wall much larger after the October 7th terrorist attack.
Shalom.
what kind of attack we can use after do DNS enum?
Have you done any deep research on DNS? What kind of techniques do these tools use in-depth? Can you suggest any paper?
how can i find out all A records for a domain.dig, nslookup, host do not work.
Thanks for tutorial, I have a question: If a website nameservers allows anonymous AXFR zone transfer, Is it a bug and will it be accepted as a bug on hackerone or other hacking platform ?
why fierce -dns doesn't work ?
ur the best man
Can you do a video on zone walking
Please make a video on misconfigure dns
Great
Sir I'm actually facing problem to perform a zone transfer. But when I used cellular data to perform DNS zone transfer it worked.....
Can you please suggest me some ideas about how to solve that problem.....??
Same happening with me whenever i do zone transfer using cellular data it is working properly but it is not working when i am using my home wifi network
hi
Bro we need discord server to talk
What about we create an unofficial one to see how it goes??
@@TheHectorshark no problem bro go a head
Do you have account in Instagram
@@ingamer5195 Where's the server?
@@darkone5194 lol well probably have to make It anyway if he doesnt answer. Add me to amiribnalmemadi in instagram
@@TheHectorsharkOk
Hello
dnsenum is not in the ubuntu repositories. After going to github.com/fwaeytens/dnsenumb cloning was my first move down the following rabbit hole. The GIThub readme for the previously mentioned page has some instructions for install with perl but it's all over the place.
(I'm not sure when or what got perl on this comp, but if you don't, you'll need it...)
I had to:
$ sudo perl -MCPAN -e shell
In retrospect later me is coming back here to say, "your perl is probably an outdated mess, mine was." So before installing stuff as instructed, start by typing:
$ Upgrade
Now go grab some lunch and come back in an hour.... you'll be halfway done but must come back for your big halftime performance where you select y/n two times within 5 min. Then it is time for the second half. Seriously I'm on an old junker laptop but this took over 1hr to finish.
Next, do this whole thing as one line:
$cpan[1]> Install XML::Writer Net::IP Net::DNS Net::Netmask Optional: Net::Whois::IP HTML::Parser WWW::Mechanize
Now go eat desert, tea, have a nap, and a snack....and it's almost done.
Followed by:
$ sudo apt install perl-doc
$ sudo apt install cpanminus
...update still going... after 1.5hrs... I'm going to go eat dinner, and catch up on some other cc's stuff, be back later with how/if this works :-)
So... I started at around 7:10pm and got it working at 9:20.
....After all of the updates and dependencies are downloaded, exit the cpan shell. You don't need to "install dnsenum" in cpan or anything like that. Assuming you cloned the git repository mentioned, from within it, (or adding the path to it), this is the command:
$ perl dsnenum.pl theaddress.foo
If you will use this often and want to save it, you can open your .bashrc file (hidden in the home/user directory), and add a line for/with the alias. Just look for other saved alias commands for context.
All of that and I was just trying to figure out who/what is hacking into my new (to me) laptop with a fresh Arch install. I don't think this was even related, it is still interesting though :-)
-Jake
@@arkiller846
The most useful thing to learn here is actually the opposite of what is shown. If you are setting up a website or server, this is one way you will be attacked. Some kid is going to download Kali Linux and start using it's tools casually without thinking. This upload is what that attack starts with. This is how they collect the information needed to target you specifically. So protect yourself against this. You could also use these tools against yourself to check if you are protected.
As for me, I installed Arch on a laptop. Every time I turn on the wifi card and watch:
$ dmesg -H -w
...I have something/someone trying to access my computer. I've gone through the Arch UFW firewall tutorial and tried to block unsolicited incoming packets. It blocks the first few attempts but eventually the attack makes it in within around 5 minutes. I don't see anything similar to this with my other laptop, also an x86 with lubuntu instead of arch. The Arch setup has 2 drives, and a W10 setup. The W10 setup is on HDD and Arch is on SSD. This is how I knew something was wrong. Five minutes after setting up the network manager with wifi credentials, I hear the hard drive spin up and someone/something trying to access data. That shouldn't happen with my setup. Arch can't mount that drive. I killed the internet and looked up the system logs. Sure enough I see someone/something come in, change my tx settings on my wifi, check my bootloader, and looked at my partitions of my SSD then tried to check the HDD, which alerted me to the issue. After that, I updated the bios and changed the admin password. I've also gone into my router and updated settings, but still I am having the same issue.
I'm here trying to learn the various tools used for both sides of this kind of attack. My problem is probably something stupid that I missed or overlooked in setting up Arch for the first time.
This upload wasn't directly related to my issue. I'm just fishing for solutions, and found this channel for the first time yesterday. I saw he uploaded a couple videos shortly after I watched the first. So I came to check them out :-)
-Jake
@@arkiller846
Find a project you are interested in first.
Like, use an old computer and router. Connect them and just figure out what you can do from one to the other.
It can even be your computer and your phone. They are probably both connected to your wifi, so you can use one to try to attack the other. If you are on android get F-Droid (search the internet for it). It's a package manager like google play but more like a linux repository. From F-Droid I have File Manager, Download Navi, Netguard, Libra PRO, Ghost Commander, Network Tools Library, Port Authority, and for fun Mupen64 Plus AE. The first 2 FM & DN let you take better control of files than Android 8 (what I'm on). LP is a better PDF viewer that doesn't spy and hide your pdf's like adobe. GC can extract zip files (tricky though, read the web instructions). NTL & PA are the ones you'll use for hacking basics. They show your internal/external IP and network info. The last one is an N64 console emulator. You can download n64 game roms and play them on your phone. I have Mario 64 now. They are a big time waster but better than the pay to play scams from google play.
All that said...I'm a hardware enthusiast. This networking, internet, and linux whitehat thing is new to me. If you have an interest in embedded hardware like me, (obligatory message: after watching everything from this channel...twice for good measure), check out my playlists. I made some content ages ago, but nothing related to this. I actually use YT as a learning tool. I save references to everything I find helpful. I also make most of these references publicly visible, and have a large range of interests. You'll probably get overwhelmed and that's not good, but it might help you find new content creators and better information, like answering questions on a subject you haven't learned to ask. I highly recommend checking out Joel over on his channel The Open Tech Lab. He was a major contributor to Pulseview. That's the GUI application for Sigrok. -open source logic analyzer software. He did a series of uploads several months ago that were outstanding examples of hacking into a little video controller board. Again that's embedded hardware specific stuff.
From what I've learned so far Python skills are pretty much mandatory for anything in the real world. This channel did a series of Python videos. That's also a good place to start.
-Jake